Research
Next-generation network technologies, such as IoT and CPS, where the real world and cyberspace cooperate, are expected to create value and services and enable a smarter society. Meanwhile, many new threats, such as defeating applications with data forgery and tampering with important factory control information, are anticipated. Specifically, in critical applications, such as autonomous control, automated operation, medical equipment, and social infrastructure, malfunction and stoppage caused by attacks can seriously affect human life, body, and social systems. While conventional information security technology has mainly focused on attacks over the network, for such new systems and usage, security designs that target the hardware directly in contact with the real world are required.
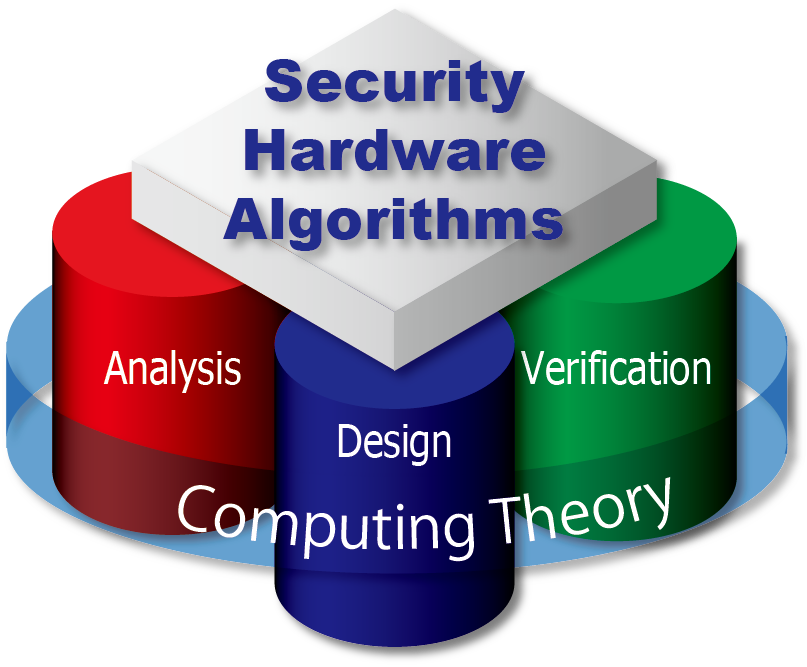
This laboratory is studying security design, evaluation, and verification for the next-generation information communication technology and systems, with the aim of building a social system so that anyone can use future services and technology safely and securely. Current research topics are 1) Cryptographic and related security computing, 2) Robust security system against various physical attacks, which are performed by physically accessing the system, and 3) Security design and evaluation of information communication systems considering the usage environment and the application field. More details on research topics are offered below. In the future, we aim to establish an integrated system security design and an evaluation technology with a wide scope, from hardware algorithm to system implementation, environment, and application.
High Performance/Secure Cryptographic Computing Theory and Its Applications
Hardware performance depends largely on the algorithm used for a given operation. Various functions in security, such as cryptography, require time-consuming and complex calculations. Therefore, it is essential to design hardware algorithms properly according to their application and the performance required. Furthermore, to use cryptographic technology in next-generation systems such as IoT and CPS, tamper resistance and detection are important design considerations, beyond conventional performance indicators such as speed, power consumption, and energy.
Homma Lab is studying the theory of hardware algorithms in a range of number systems used in security functions, e.g. Galois fields, and has successfully developed the highest efficiency advanced encryption standard (AES) hardware in the world, for instance, as well as high-performance RSA hardware resistant to physical attacks. In addition, we are working on design and verification technology for hardware algorithms. Specifically, we have succeeded in verifying the modern cryptographic hardware that conventional methods could not.
At present, we are developing an automatic synthesis system, called arithmetic module generator (AMG), to generate arithmetic hardware algorithms, as one of our research results. AMG consists of two generators: (1) I-AMG for integer arithmetic hardware and (2) GF-AMG for Galois-field arithmetic hardware, and it automatically generates hardware description language (HDL) descriptions of the arithmetic hardware based on the number system and the algorithm specified. The functionality of the hardware generated is completely verified by the formal verification method developed by our research group. AMG is available ">here.
Examples of research topics:
- Highly efficient, high performance, or light weight cryptographic hardware algorithms
- Tamper-resistant cryptographic hardware algorithms
- Arithmetic hardware algorithms to facilitate the detection of malicious hardware
- Formal design and verification of hardware algorithms on Galois fields
- Formal verification of security properties
Hardware security for embedded systems
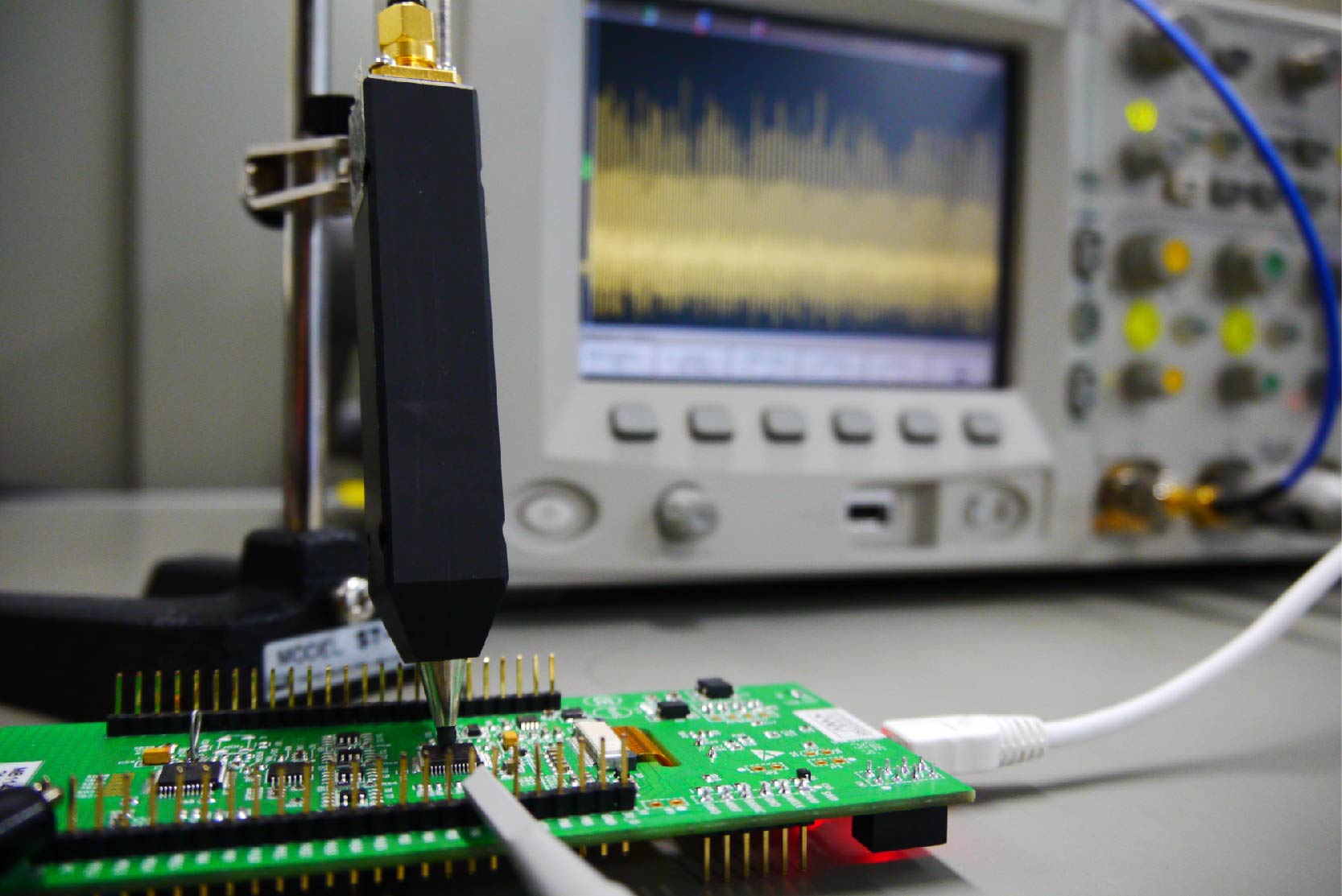
In the next-generation society where devices around us are all connected to the network, even those with poor computational resources (e.g., sensors and small terminals) that are in contact with the real world can be targeted by attackers. This suggests that such devices must be properly equipped with security functions. They are also expected to be resistant to physical attacks as they can be physically accessed by attackers. Regarding components such as IC and SIM cards, we must also assume that the owners themselves can become attackers.
Under these various constraints and attack scenarios, we are studying security design and analysis technologies for embedded systems equipped with security functions. As an example, we have developed a design and security evaluation platform for cryptographic embedded systems. The platform is currently being used by universities, research institutes, and companies, worldwide. In addition, we are engaging in research and development with cutting-edge technologies such as reactivity countermeasures to instantaneously detect micro-probing to hardware.
Examples of research topics:
- Side-channel attacks on cryptographic systems and countermeasures
- Reactive countermeasure technology to prevent electromagnetic attacks
- Efficient implementation of cryptographic hardware for secret computation
- Design and evaluation platform for secure embedded systems
- Highly reliable systems using physical unclonable functions
- High-efficiency and tamper-resistant hardware design for post-quantum cryptography
Security system conscious of usage environment and applications
With the remarkable development of information technology in communications, terminals such as smartphones have permeated many aspects of our daily lives. In addition, in the future we expect innovative applications, such as smart cities, mobile systems including self-driving vehicles and small satellites, and custom-made medical devices and healthcare, on the premise of network connectivity. From now on, security by design will be essential to handle the increasing diversification in usage environment and applications.
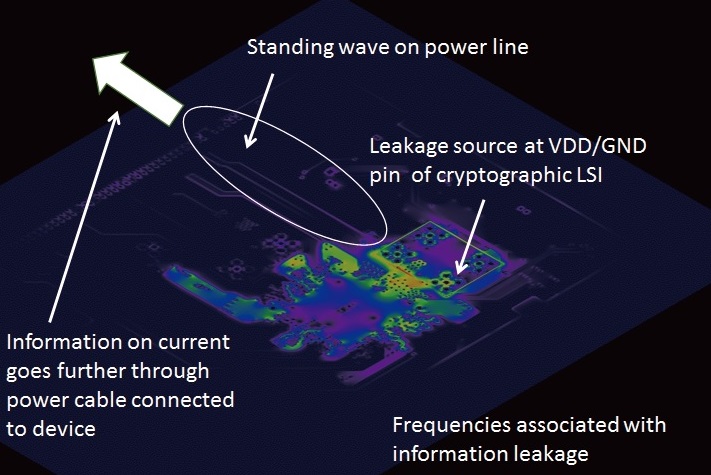
In keeping with anticipated next-generation usage environments and applications, we are pursuing research and development on security system design and evaluation technologies. From the viewpoint of usage environment, we are studying the mechanism of electromagnetic information leakage from smart devices used in public places and the related security evaluation technology. For example, we have successfully visualized electromagnetic information leakage from a cryptographic hardware and received the best paper award at the most important international conference in the field of electromagnetic compatibility (EMC). From the viewpoint of next-generation applications, we are studying security systems for connected cars and small satellites/rockets through collaborative research with companies.
Examples of research topics:
- Electromagnetic security evaluation and visualization of smartphones and tablets
- Side channel security for cloud services
- Nonvolatile memory security for AI systems
- Hardware security for connected cars
- Secure avionics for small satellites and rockets